Clickjacking Attack
What is clickjacking
A clickjacking attack deceives a user into clicking an element of a webpage that is hidden or misrepresented as another element. Due to this, users may unintentionally download malware, browse malicious websites, disclose sensitive information or login credentials, send money, or make online purchases.
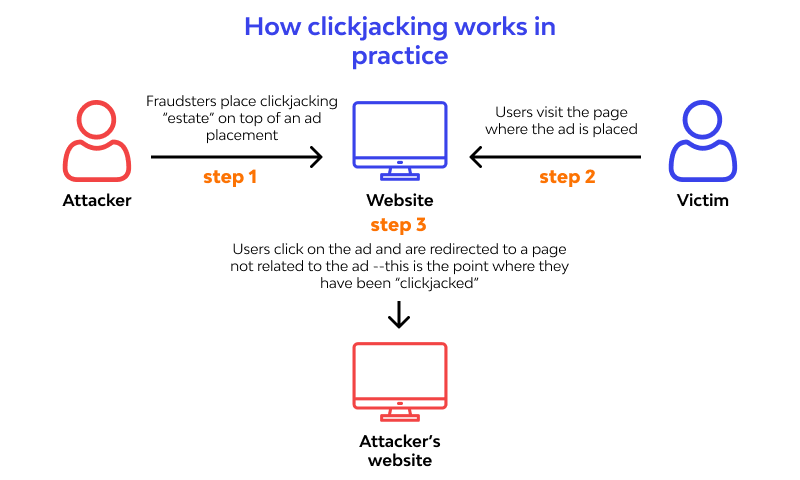
 The most common method of clickjacking is to overlay the page the user sees with an invisible page or HTML element that is displayed inside of an iframe. In reality, the user is clicking an invisible element on the additional page that is transposed on top of the visible page when they think they are clicking the visible page.
The most common method of clickjacking is to overlay the page the user sees with an invisible page or HTML element that is displayed inside of an iframe. In reality, the user is clicking an invisible element on the additional page that is transposed on top of the visible page when they think they are clicking the visible page.
A valid page that the user did not plan to see or a malicious page could both be the invisible page. An example would be a page on the user’s banking website that permits a money transfer.
There are various clickjacking attack variations, including:
- A method known as “likejacking” tricks users into “liking” a website they didn’t really want to by manipulating the Facebook “Like” button.
- Cursorjacking is a method of user interface (UI) redressing that moves the cursor from the position the user perceives to a different position. Cursorjacking makes use of flaws in Flash and the Firefox web browser, both of which have since been addressed.
Clickjacking attack example
 The attacker builds a visually appealing page that offers the user a free trip to Tahiti.
The attacker builds a visually appealing page that offers the user a free trip to Tahiti.
The attacker checks in the background to see if the user is signed into his banking site, and if so, loads the screen that permits the transfer of funds and enters his bank information using query parameters.
The user may see the “Confirm Transfer” button perfectly aligned over the “Receive Gift” button on the bank transfer page, which is presented above the free gift page in an unseen iframe.
When a user sees the page, they choose to “Book My Free Trip.”
The “Confirm Transfer” button has actually been activated by the user when they are actually clicking on the unseen iframe. Money is transferred to the assailant.
The user is taken to a website with details on the free gift after being redirected (not knowing what happened in the background).
This example shows how a clickjacking attack works by showing how the malicious activity (in this case, on the bank website) was carried out by the user while they were actually signed into their own account.
Clickjacking mitigation
There are two standard strategies for stopping clickjacking:
- Client-side techniques: Frame busting is the most popular. Although client-side techniques may be useful in some circumstances, they are not regarded as best practices because they are simple to get around.
- The most popular server-side technique is X-Frame-Options. Security professionals advise using server-side techniques as a viable countermeasure to clickjacking.
Mitigating clickjacking with X-Frame-Options response header
If a browser should be permitted to render a page inside a FRAME> or IFRAME> tag, it is indicated by the X-Frame-Options response header that is supplied as part of the HTTP response of a web page.
The X-Frame-Options header can take one of three values:
- DENY – prohibits any domain from displaying this page inside a frame
- SAMEORIGIN – only works within the current domain and allows the current page to be displayed in a frame on another website.
- Only in a specific URI, such as www.example.com/frame-page, does the ALLOW-FROM URI directive allow the current page to be shown in a frame.
Using the SAMEORIGIN option to defend against clickjacking
Publishers of online material can utilize X-Frame-Options to stop intruders from using their own content in an unseen frame.
The most secure choice is DENY, which forbids the use of the current page in a frame. SAMEORIGIN is used more frequently since it permits the use of frames but restricts them to the current domain.
X-Frame-Options’ restrictions
- The X-Frame-Options header must be returned as part of the HTTP response for each individual page in order to enable the SAMEORIGIN option across a website (cannot be applied cross-site).
- Due to the fact that X-Frame-Options does not offer a whitelist of permitted domains, it is ineffective for multi-domain sites that require the display of framed content between them.
- It is not possible to show the same page as a frame on the current website and an external website since only one option can be utilized on a single page.
- Not all browsers support the ALLOW-FROM setting.
In the majority of browsers, X-Frame-Options is a deprecated option.
Test for clickjacking: Is your website at risk?
Making an HTML page and attempting to embed a sensitive page from your website in an iframe is a simple test you may perform to see if your website is susceptible to clickjacking. It is crucial to run the test code on a different web server because this is how a clickjacking attack typically behaves.
Use the code provided in the OWASP Testing Guide, such as this:
<html> <head> <title>Clickjack test page</title> </head> <body> <p>Website is vulnerable to clickjacking!</p> <iframe src="http://www.yoursite.com/sensitive-page" width="500" height="500"></iframe> </body> </html>
Examine the HTML page in a browser and give it the following grade:
- The page is clickjackable if the text “Website is vulnerable to clickjacking” appears and the content of your sensitive page displays beneath it.
- The page is not susceptible to the most basic type of clickjacking if simply the text “Website is vulnerable to clickjacking” displays and you do not view the content of your sensitive page.
However, more research is required to determine which anti-clickjacking techniques are employed on the page and whether attackers can get around them.
lessen clickjacking attacks
 A website must first be infiltrated in order to perform clickjacking, which WAF guards against. Additionally, you should check that the resources on your site are delivering the appropriate X-Frame-Options HTTP headers, which would stop some of the content on your site from being framed in other pages or on domains other than your own.
A website must first be infiltrated in order to perform clickjacking, which WAF guards against. Additionally, you should check that the resources on your site are delivering the appropriate X-Frame-Options HTTP headers, which would stop some of the content on your site from being framed in other pages or on domains other than your own.
What is used to prevent clickjacking?
By means of the X-Frame-Options header
Asking the browser to deny any attempt to load your website within an iframe is a better strategy to thwart clickjacking attacks. Sending the X-Frame-Options HTTP header is one way to achieve it.
Is clickjacking a XSS attack?
Clickjacking as a method of delivery for Blind XSS
The basic idea behind XSS attacks, including Blind XSS, is that the attacker can create and inject a malicious script into the HTML page that the browser processes for display, forcing it to execute the payload.
How can clickjacking attack be prevented?
Make sure your website can’t be iframed by a malicious site if you don’t want it to be used in a clickjacking assault. This can be accomplished either directly instructing the browser using HTTP headers, or in earlier browsers, by utilizing client-side JavaScript (frame-killing).
What is an example of clickjacking defenses?
You must make sure that a malicious site cannot embed your website in an iframe in order to prevent it from being utilized in a clickjacking attack. The browser can be instructed directly using HTTP headers, or with earlier browsers, client-side JavaScript can be used (frame-killing).
How do clickjacking attacks work?
The practice of “UI redress attack,” sometimes known as “clickjacking,” involves an attacker using several transparent or opaque layers to deceive a user into clicking a button or link on a different website when they actually meant to click on the top-level page.
What is the difference between clickjacking and phishing?
What distinguishes phishing from clickjacking? Since phishing scams require direct communication with the victim, they differ slightly from clickjacking. Typically, an attacker will send a phone email impersonating a reputable business in an attempt to deceive recipients into responding with personal information.
