07Sep
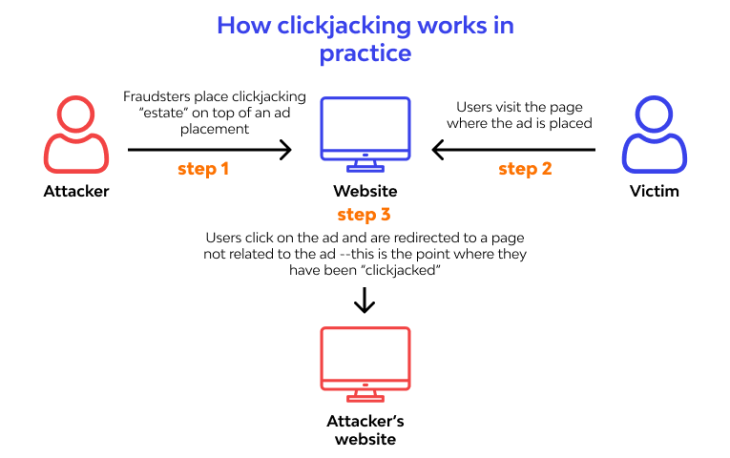
In a recent interview with Security Weekly, Invicti security researcher Sven Morgenroth gave an overview of HTTP security headers. Many HTTP headers that can strengthen online application security and defend against cross-site scripting, clickjacking, and…